Examining nested stack traces
I often read Java Stack traces bottom up when I examine them for the first time – simply because this is the code path which was executed when the exception occurred. However, it can happen that the last line of a stack trace shows something like ... 2 more – so, one might ask why can’t the runtime just dump those missing lines, along with all the other stack trace elements? Real life server stack traces sometimes contain dozens of lines, it should not matter to print those additional lines, right? And often those lines contain just the information you require to see from where the problematic code which caused the exception was called … The thing is: those lines are actually in the stack trace. Lets consider this example:
Exception in thread "main" java.lang.RuntimeException: java.lang.RuntimeException: Exception thrown at com.example.TraceTest.doSomething(TraceTest.java:13) at com.example.TraceTest.run(TraceTest.java:6) at com.example.TraceTest.main(TraceTest.java:22) Caused by: java.lang.RuntimeException: Exception thrown at com.example.TraceTest.throwAnException(TraceTest.java:18) at com.example.TraceTest.doSomething(TraceTest.java:11) ... 2 more
As you can see, the last line reads ... 2 more, but it might be crucial for the further analysis to know from where the doSomething() method was called. In order to get this information, we need to look further up in the stack trace: There, we again find the doSomething() method at the top and see that it was called from the run() method. In other words, the initial entry point for the code flow is the last element of the first stack trace block – from there, we can follow to the next stack trace block to see where the exception was finally thrown:
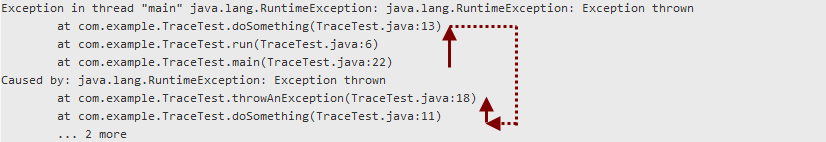
The reason for this is that the original exception was wrapped as nested exception into another exception. The following is the code which was used for the test above:
package com.example;
public class TraceTest {
public void run() {
doSomething();
}
private void doSomething() {
try {
throwAnException();
}catch(RuntimeException re) {
throw new RuntimeException(re);
}
}
private void throwAnException() {
throw new RuntimeException("Exception thrown");
}
public static void main(String[] args) {
new TraceTest().run();
}
}
Real stack traces might also contain more than one nested exception, so it might be necessary to follow them more than once.
![]() In any case, the stack trace still contains the whole code path from the entry point (usually main) to the place where the exception was thrown.
In any case, the stack trace still contains the whole code path from the entry point (usually main) to the place where the exception was thrown.
See also how to print the full stacktrace in java on StackOverflow.